The ongoing stories in the press are hurting charities who are being seen to be treating decent people – particularly vulnerable people – monstrously unfairly. The press and media are giving consumers an ever clearer perception of the charity sector as being irresponsible, uncaring and aggressive in their treatment of donors. And it does the data industry no favours at all.
Category Archives: General Information
Data Privacy is now precious …
EU Data Protection Laws – why it’s time to get ready
 EU Data Protection – Change is Coming
EU Data Protection – Change is Coming
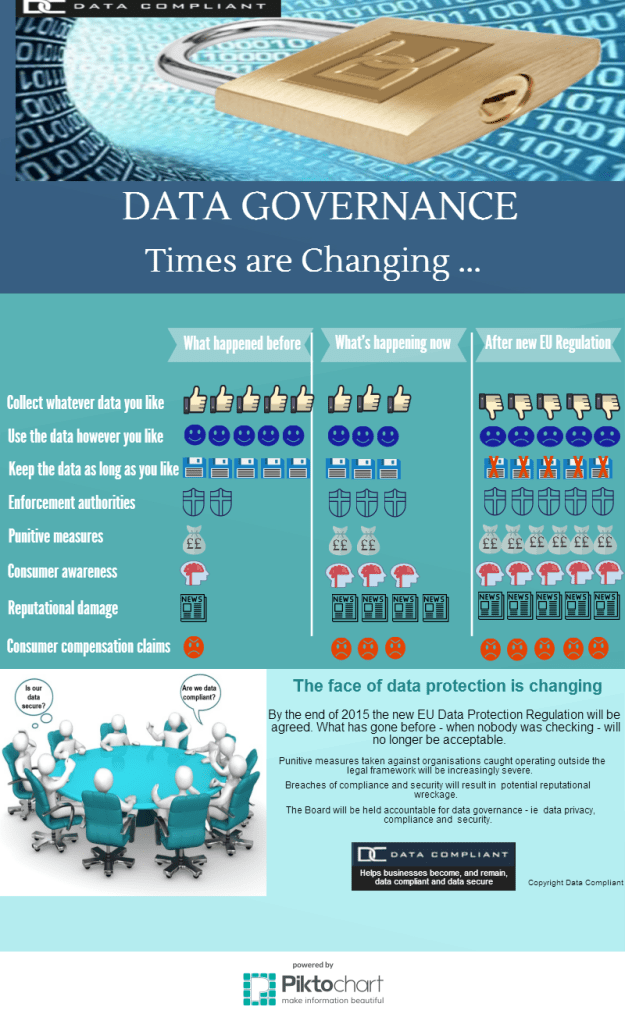
The new EU data protection law is getting ever closer. The clock is ticking, with major changes on the horizon relating to the way businesses will be allowed to collect, hold, store and use personal data.
New EU Regulation – what will change?
The changes to the law fall into two main areas
-
Responsibility and Accountability …
… which will require organisations to demonstrate stringent data governance and robust data protection policies, procedures, processes and training, starting with the Board.
-
Marketing …
… which will impact consent (which must be obtained fairly, and be unambiguous and explicit), and will impose restrictions around tracking and profiling.
You’ll find more information about the upcoming DPA changes in relation to marketing and accountability in the guest blog I wrote for All Response Media.
When will the new EU Regulation become Law?
This has been the subject of much discussion. Justice and Home Affairs Ministers agreed amendments to the Commission Text in June, and three-way negotiations are now taking place between the EC, Parliament and Justice and Home Affairs Ministers.
It is expected that this process will be completed by December 2015, in which case the Regulation will be passed in Brussels in early 2016, and become UK law in late 2017 / early 2018.
So why do I need to start now?
While it may seem that a couple of years is plenty of time to get ready, failing to react until the big shake-up actually arrives is likely to cause chaos and confusion throughout all areas of your business.
Responsibility and accountability for the new legal requirements around data protection must lie with the Board in order to be embedded throughout all areas of the business – from sales and marketing to IT, HR to Customer Services. With that in mind, and given the huge emphasis on accountability and governance, preparation and planning are essential, and businesses need to start looking at their data governance, compliance and security measures right now.
How can Data Compliant help?
The protection of the personal data your company holds needs to be of paramount importance – it will no longer be acceptable to fall short in terms of accountability, or responsibility, or to rely on loopholes in the current legislation. So please get in touch if you you would like to discuss the implications of the new legislation, and to understand your obligations around data governance, security and compliance. Have a look at our website, call 01787 277742, or email victoria@datacompliant.co.uk
Data Breaches UK – Key Stats at a Glance
The 2015 UK data breaches report shows significant rises in numbers and costs of data breaches, with growth shown in my previous blog, Data Breaches – OUCH! . The infographic below summarises the key data breach stats from 2014, including a nod to the impact of new technology.
* All stats taken from 2015 Information Security Breaches Survey commissioned by HM Government – survey conducted by PwC in association with Infosecurity Europe
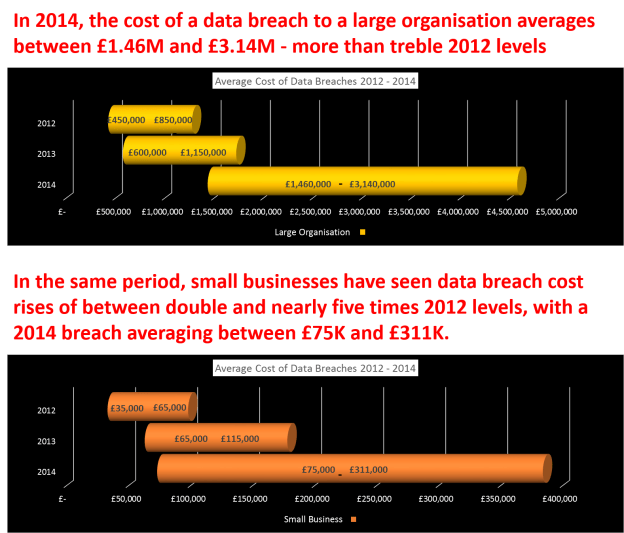
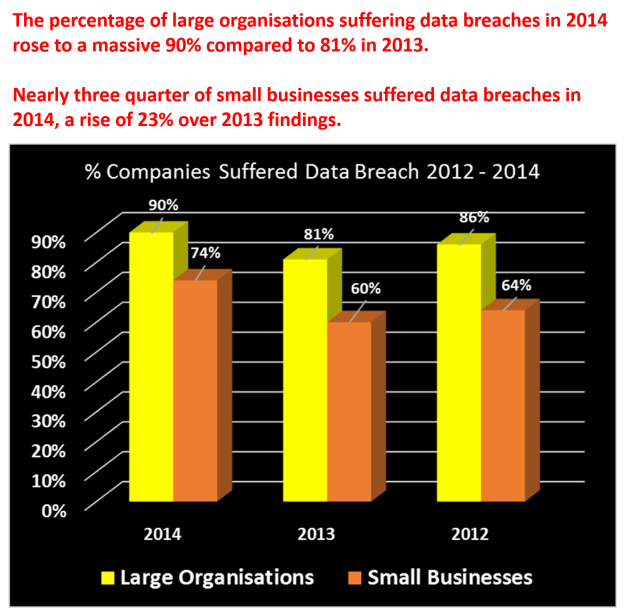
Data breaches … OUCH!
Alarming data breach statistics are shown in the latest survey from HM Government*, with costs increasing to prohibitive levels for businesses large and small.
Data Breach Costs
Think a data breach can’t happen to you? Think again …
* All stats taken from 2015 Information Security Breaches Survey commissioned by HM Government – survey conducted by PwC in association with Infosecurity Europe
Protect your data …
The protection of your company data must be of paramount importance to you, so please get in touch if you you would like to discuss the ever-changing issues surrounding data security and the steps you can take to keep your data safe. Call 01787 277742 or email victoria@datacompliant.co.uk
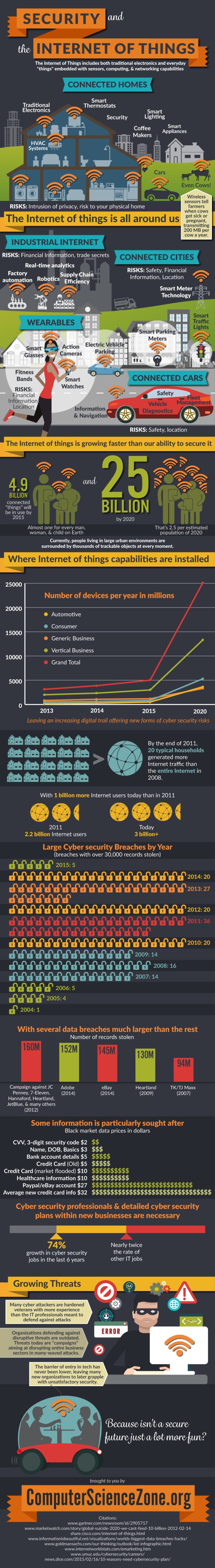
Security and the Internet of Things
I was invited by ComputerScienceZone to share this fascinating infographic on my site – so here it is – a fascinating insight into the diversity and number of “things”, combined with the risks associated with the rapid growth and poor security.
Data Security – A Summary
 When we talk about data security what do we actually mean?
When we talk about data security what do we actually mean?
Data security means protecting data, such as database, from destructive forces and from the unwanted actions of unauthorised users.
In the UK, the Data Protection Act is used to ensure that personal data is accessible to those whom it concerns, and provides redress to individuals if there are inaccuracies. This is particularly important to ensure individuals are treated fairly, for example for credit checking purposes. The Data Protection Act states that only individuals and companies with legitimate and lawful reasons can process personal information and cannot be shared.
The international standard ISO 27001 covers data and information security. Information security is the practice of defending information from unauthorised access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction. It is a general term that can be used regardless of the form the data may take (e.g. electronic, physical)
So what is Data Security?
- Data is any type of stored digital information.
- Security is about the protection of assets.
- Prevention is the measures taken to protect your assets from being damaged.
- Detection is the measures taken to allow you to detect when an asset has been damaged, how it was damaged and who damaged it.
- Reaction is the measures that allow you to recover your assets.
- Confidentiality ensures that that data is only read by the intended recipients.
- Integrity ensures that all of the data has not been corrupted from its original source.
- Availability guarantees that the data is usable upon demand.
- Accountability is audit information that is kept and protected so that security actions can be traced to the responsible party.
Audit Standards
Data Security is subject to several types of audit standards and verification, the most common are ISO 27001, PCI, ITIL. Security Administrators are responsible for creating and enforcing a policy that conforms to the standards that apply to their business.
IT certification audits are generally carried out by 3rd parties although regular internal audits are recommended. Clients can also carry out audits before they begin doing business with a company to ensure that their clients data is secured to their standards.
Security Policy
A security policy is a comprehensive document that defines a company’s methods for prevention, detection, reaction, classification, accountability of data security practices and enforcement methods. It generally follows industry best practices as defined by ISO 27001, PCI, ITIL or a mix of them. The security policy is the key document in effective security practices. Once it has been defined it must be implemented and modified and include any exceptions that may need to be in place for business continuity. Most importantly all users need to be trained on these best practices with continuing education at regular intervals.
Securing data
Data needs to be classified in the security policy according to its sensitivity. Once this has taken place, the most sensitive data has extra measures in place to safeguard and ensure its integrity and availability.
All access to this sensitive data must be logged. Secure data is usually isolated from other stored data and it is important that controlling physical access to the data centre or area where the data is stored is implemented.
Active Directory for example is used by many companies and is a centralised authentication management system that is used to control and log access to any data on the system.
Encryption of the sensitive data is critical before transmission across public networks. The use of firewalls on all publicly facing WAN connections needs to be in place and also the deployment of VLANs’ to isolate sensitive departments from the rest of the network. It is important to shut down unused switch ports. If Wi-Fi is deployed then it is important to use authentication servers to verify and log the identity of those logging on. Finally the deployment of anti-virus and malicious software protection on all systems.
Monitoring
Sometimes you will be surprised what you can find by simply walking around and look for passwords in the open, unattended screens.
Ensure that Event Viewer and Log Files are maintained this provides the audit trail. An Intrusion Detection/ Protection systems (IDS/IPS) to monitor the network and system activities for malicious activities or policy violations. Set up SNMP monitoring servers to monitor and alert for everything as this will alert Administrators to everything from unusual bandwidth usage to hardware failure. It is key to know what’s going on with your systems and network.
Documentation is also important, detailed network maps should be available as these maps make it easier to spot security weak points and any flaws in the design that could impact the data security.
You should also consider a network scanner that probes devices to ensure that they are secure. A network scanner will probe and report old out of date software, open ports and the give details on any potential exposures. Networks scans should be scheduled on a regular basis.
Keep up to date and stay Informed
Review log files regularly of any publicly facing server to see what types of attacks are being run against your enterprise.
Trade publications discuss the latest threats and technologies keeps you updated on the latest attack trends. It is important to understand the technology stack that you are protecting and the technology that is used to attack it.
User Education
Something which tends to not be given the required level of importance is user education. All relevant security policies must be clearly explained to the end users. A clear explanation of the consequences for violating these polices must also be explained. The end user needs to sign a document acknowledging that they understand the policies and consequences for violating these policies.
Enforcement
Any enforcement must obtain executive authority to enforce the business policies and procedures. This must be based on a systematic approach of warnings and punishments.
The author, Tony Schiffman, is Data Security Director at Data Compliant. If you have any concerns about your organisation’s data security or vulnerabilities and you’d like a chat, please call Tony on 01787 277742 or email dc@datacompliant.co.uk
Data Security – Phishing
45% of phishing attacks are successful, according to Google’s December 2014 report. Indeed, the infamous 2013 Target data breach was due to a successful spear phishing attack on one of the company’s suppliers. The reported cost to the business was a massive $162M plus additional expenses resulting from class action lawsuits and reputational damage.
Many data breaches are a direct result of the attacker using individuals or employees to access systems or data, and it’s worth noting that 58% of large organisations and a third of SMEs fall prey to staff-related data breaches (*UK 2014 Information Security Breaches Survey).
With that in mind, I thought it would be helpful to summarise some points to help recognise and deal with phishing emails.
What is phishing?
Phishing is a deceptive means of trying to acquire personal information such as your identity or data that you hold and access – for example your user name, passwords, credit card details, contact directories and so on. Phishing is typically carried out by email or instant message, which may ask you to provide the data directly, or it may send you to a website or phone number where you will be asked to provide data.
Why Phishing Works
A phishing effort can be hard to recognise, particularly if it comes from a source that you are inclined to trust – for example a friend or colleague (who may have been phished themselves), or your bank, social media site, telephone provider etc.
- Phishing emails are designed to look like real emails from real, sometimes large, reputable organisations.
- They are likely to seem to come from an organisation or individual you know and would expect to hear from – for example your bank or building society, your insurer, a business with whom you are in regular contact, your social networking sites, an online auction site or even a friend whose email sits in your address book
- They may look absolutely authentic, including using legitimate logos
- They may well contain information that you would not expect a scammer to know – for example personal data (that they may, for example, have picked up from one of your social networking sites)
- They may include links to websites which will require you to enter personal information – and that website may also look very similar to the legitimate website it is pretending to be.
How to spot a phishing email
There are ways to recognise and avoid being caught out by fraudulent emails or the links they contain.
- Are you expecting the email you’ve just received? Any email which asks you for personal information or log in details or to verify your account must be treated with caution – most reputable companies will never ask for your personal details in an email
- Don’t be pressured just because the email looks urgent
- Beware of attachments – these may pretend to be an order summary or an invoice for immediate payment or a receipt or any manner of other things. If you haven’t placed an order, or your bill is already paid, then be careful. If in doubt, simply do not open the attachment.
- Check the email’s spelling, grammar and formatting – if they’re not correct, treat the email as suspicious
- Never respond to an email that asks you to update your credit card or payment details
- Watch out for free giveaways with links to websites – it’s likely that such websites will attempt to embed a virus into your computer which allows them to capture your keystrokes to get your login details or financial details such as your bank account
How to spot a phishing link?
Such links are likely to include all or part of the legitimate website address.
- Be aware than any change to the legitimate address may lead to a false website – a spelling mistake, a missing letter – just one character’s difference can take you somewhere you just don’t want to go,
- It is generally safer to go to the online website using your own bookmarks or by typing in the website address yourself
- Where a website link is provided, it may be “masked” so that what you see will not take you where you expect. Using your mouse to “hover” your cursor over the link may enable you to see the actual address – DO NOT CLICK ON ANY LINK unless or until you are completely certain it is the legitimate website
Protect against phishing
Being aware and understanding how to spot a potential phishing effort is helpful, but additional steps should be taken to protect your computer and system against such attacks. There is no single solution – the best option is to adopt a multi-layered approach:
- Good security software will help to prevent successful phishing by spotting “bad” links and blocking fake websites.
- While not providing all-encompassing protection, anti-virus, anti-spyware and anti-malware applications should be used, and kept up-to-date. Ensure that at least two different supplier technologies are in operation.
- Ensure that all firewall settings should be used and updated regularly to help prevent phishing and block attacks.
- Subscribe to cyber-intelligence services which may be used to identify on-line threats, misrepresentations, or online fraud’s targeting brands – for example, RSA or Verisign
- Ensure that applications and operating systems are up-to-date and fully patched
What to do if you have opened a phishing email
Just opening the email is unlikely to cause a problem. However, it is helpful to report phishing emails:
- To the ISP (internet service provider) that was used to send you the email so that ISP provider can close the sender’s email account
- If “report spam” buttons are available, use them
- Report the email to the legitimate organisation the sender is pretending to be
- Delete the email from your device
- Inform your IT department and / or your data protection / data compliance / data security officer
- Report the phishing email to Action Fraud – the UK’s national fraud and internet crime reporting centre – at https://reportlite.actionfraud.police.uk/
What to do if you click on a phishing link
- Immediately run a virus check on your computer whether or not you have provided any personal details
- Change your password for organisation which the phisher is mimicking
- If you use the same password for multiple accounts, you need to change all these passwords too
- Notify the relevant financial organisation(s) if you have entered banking or credit card information
- Inform your IT department and / or your data protection / data compliance / data security officer
- Report the phishing email to Action Fraud at https://reportlite.actionfraud.police.uk/
As phishing attacks predominantly targeting end-users, it is a good idea to invest in a security education and awareness programme to raise the profile of risk. It’s also helpful to include your clients in such a programme.
If you have any concerns about your organisation’s vulnerability to phishing attacks and you’d like a chat about staff training or prevention, just call 01787 277742 or email dc@datacompliant.co.uk
Data Compliant Services
ISO 27001 Certification – who needs it?
It’s becoming an increasingly essential part of due diligence that a data controller, when appointing a data processor, will ask one simple question: “Do you have ISO 27001 Certification?” Given that data controllers are the liable parties for any data breaches or lack of compliance, they need to be certain their data is to be processed safely. So if the answer is “no”, the processor is unlikely to win the contract unless they have some other extraordinary and unique competitive advantage.
I was going to write a blog about why ISO 27001 certification is so important. Then I thought it would be simpler just to show you. It’s all about protecting your business from potential breaches.
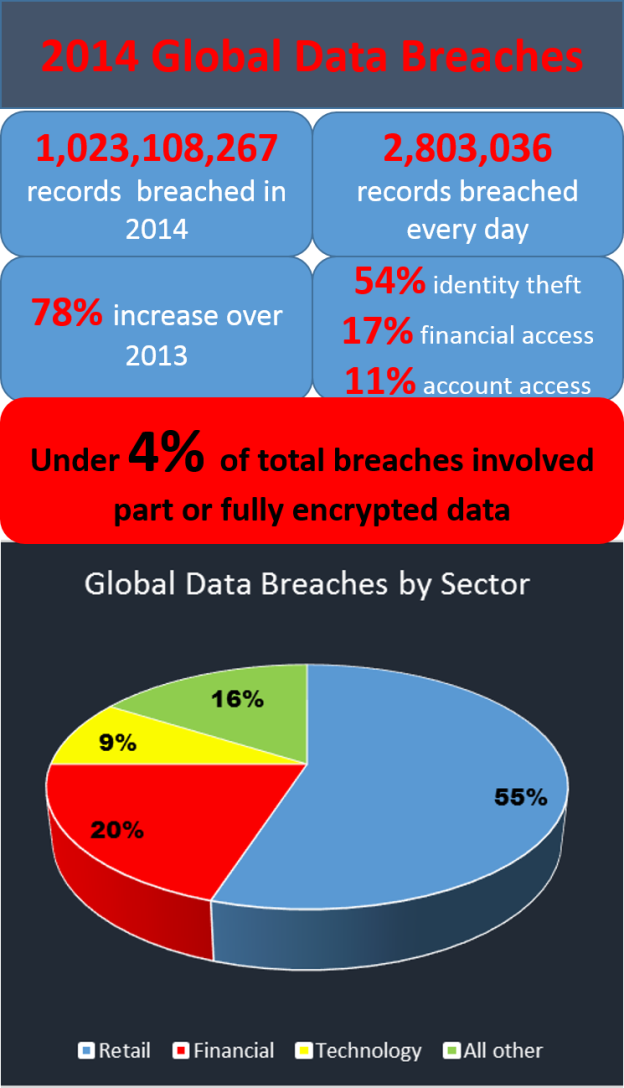 From the stats above, taken from the 2014 Year of Mega Breaches and Identity Theft, it’s clear to see:
From the stats above, taken from the 2014 Year of Mega Breaches and Identity Theft, it’s clear to see:
- the US is clearly the largest target, but UK has second largest number of breaches
- retail organisations suffered the greatest volume of data loss in 2014
- only 4% of data breaches involved encrypted data – an astonishing statistic which tells us:
- encrypted data is harder to breach
- given the critical nature of encryption in data protection, the sheer volume of unencrypted data is staggering – too many organisations are simply not taking the most basic of steps to help keep their data secure
ISO 27001 is an international standard for data security management, providing a risk-based approach to data security that involves a data governance standard that is embedded throughout the business covering processes, technology, employees and training.
In the past, obtaining ISO 27001 certification has been a time-consuming, arduous and costly exercise. Now, however, the whole process of creating the gap analysis, providing robust policies and procedures, and obtaining certification can be made much simpler.
If you’d like to know more about getting ISO 27001 quickly, simply and cost-effectively, please get in touch on 01787 277742 or email victoria@datacompliant.co.uk – we’ll be happy to have a chat and answer your questions
EU versus Google – £12 million DPA fine
 The pressure on Google over European data privacy issues has been ongoing for several years as EU data protection watchdogs attempt to bring the organisation – and other huge US companies – into line with European data protection principles.
The pressure on Google over European data privacy issues has been ongoing for several years as EU data protection watchdogs attempt to bring the organisation – and other huge US companies – into line with European data protection principles.
The latest threat to Google comes from Holland, where the Dutch DPA has threatened Google with a fine of up to 15M euros for breaking local laws over how it can use user data. Google has been given until the end of February 2015 to change the way it handles personal data, before the fine is levied.
Online behaviour used to target advertising
So what has Google done wrong? The issue is over the way Google uses data about people’s online behaviour to tailor advertisements. Google builds up a profile for every one of its users based on keywords used in searches, email messages, cookies, location data – even video viewing habits. However, it does not inform its data subjects that it is collecting and using data in this way, and nor does it obtain consent.
Google’s Data Assets
Google’s data is a core asset for the business, and other businesses like it. One of Google’s key data privacy issues is that the company has merged all its separate privacy policies into one policy which allows Google to share its user data across all its services – for example, Gmail data and search engine data can be used and combined across the company. In addition, there is no opt-out for the data subject.
From Google’s point of view, its customer profiling is enhanced considerably by this activity – and advertising to targeted customers is Google’s core revenue stream. Google also uses customer data to drive new products such as Google now (appointment based app, giving details on how to get to your appointment, where it is, what are the traffic conditions and what time to leave) – a great concept, but one that would be useless without Google’s ability to collect and use data from its users.
It has been clear for some time that the EU is determined to take on the challenge of the giant UK search engines and social media platforms, and curb the way they use data. Because Google has such a vast share of the market, it, in particular, regularly comes under fire from the EU.
Google Privacy Policy – Fairness and Transparency
The requirement for additional permissions or opt-outs may be more problematic than helpful for Google customers. But fairness and transparency is an issue that Google could address relatively simply – as a minimum the customer should be informed about the data Google is collecting about him or her, why it is being collected and how it is being used. And a little bit of creativity in the wording would serve to illustrate the benefits to the customer.
The single privacy policy makes such transparency difficult. So perhaps the simplest solution is to re-establish separate privacy policies for each of its business areas. That might at least serve to reassure not only the EU, but also the US data protection authorities who have also expressed concerns over Google’s single privacy policy.
Your thoughts and views are always welcome – please add your comments below. If you have any concerns about your data compliance in general or the impact of EU changes in your business, contact us on 01787 277742. Or email victoria@datacompliant.co.uk