The ongoing stories in the press are hurting charities who are being seen to be treating decent people – particularly vulnerable people – monstrously unfairly. The press and media are giving consumers an ever clearer perception of the charity sector as being irresponsible, uncaring and aggressive in their treatment of donors. And it does the data industry no favours at all.
Tag Archives: data compliance
EU Data Protection Laws – why it’s time to get ready
 EU Data Protection – Change is Coming
EU Data Protection – Change is Coming
The new EU data protection law is getting ever closer. The clock is ticking, with major changes on the horizon relating to the way businesses will be allowed to collect, hold, store and use personal data.
New EU Regulation – what will change?
The changes to the law fall into two main areas
-
Responsibility and Accountability …
… which will require organisations to demonstrate stringent data governance and robust data protection policies, procedures, processes and training, starting with the Board.
-
Marketing …
… which will impact consent (which must be obtained fairly, and be unambiguous and explicit), and will impose restrictions around tracking and profiling.
You’ll find more information about the upcoming DPA changes in relation to marketing and accountability in the guest blog I wrote for All Response Media.
When will the new EU Regulation become Law?
This has been the subject of much discussion. Justice and Home Affairs Ministers agreed amendments to the Commission Text in June, and three-way negotiations are now taking place between the EC, Parliament and Justice and Home Affairs Ministers.
It is expected that this process will be completed by December 2015, in which case the Regulation will be passed in Brussels in early 2016, and become UK law in late 2017 / early 2018.
So why do I need to start now?
While it may seem that a couple of years is plenty of time to get ready, failing to react until the big shake-up actually arrives is likely to cause chaos and confusion throughout all areas of your business.
Responsibility and accountability for the new legal requirements around data protection must lie with the Board in order to be embedded throughout all areas of the business – from sales and marketing to IT, HR to Customer Services. With that in mind, and given the huge emphasis on accountability and governance, preparation and planning are essential, and businesses need to start looking at their data governance, compliance and security measures right now.
How can Data Compliant help?
The protection of the personal data your company holds needs to be of paramount importance – it will no longer be acceptable to fall short in terms of accountability, or responsibility, or to rely on loopholes in the current legislation. So please get in touch if you you would like to discuss the implications of the new legislation, and to understand your obligations around data governance, security and compliance. Have a look at our website, call 01787 277742, or email victoria@datacompliant.co.uk
ISO 27001 Certification – who needs it?
It’s becoming an increasingly essential part of due diligence that a data controller, when appointing a data processor, will ask one simple question: “Do you have ISO 27001 Certification?” Given that data controllers are the liable parties for any data breaches or lack of compliance, they need to be certain their data is to be processed safely. So if the answer is “no”, the processor is unlikely to win the contract unless they have some other extraordinary and unique competitive advantage.
I was going to write a blog about why ISO 27001 certification is so important. Then I thought it would be simpler just to show you. It’s all about protecting your business from potential breaches.
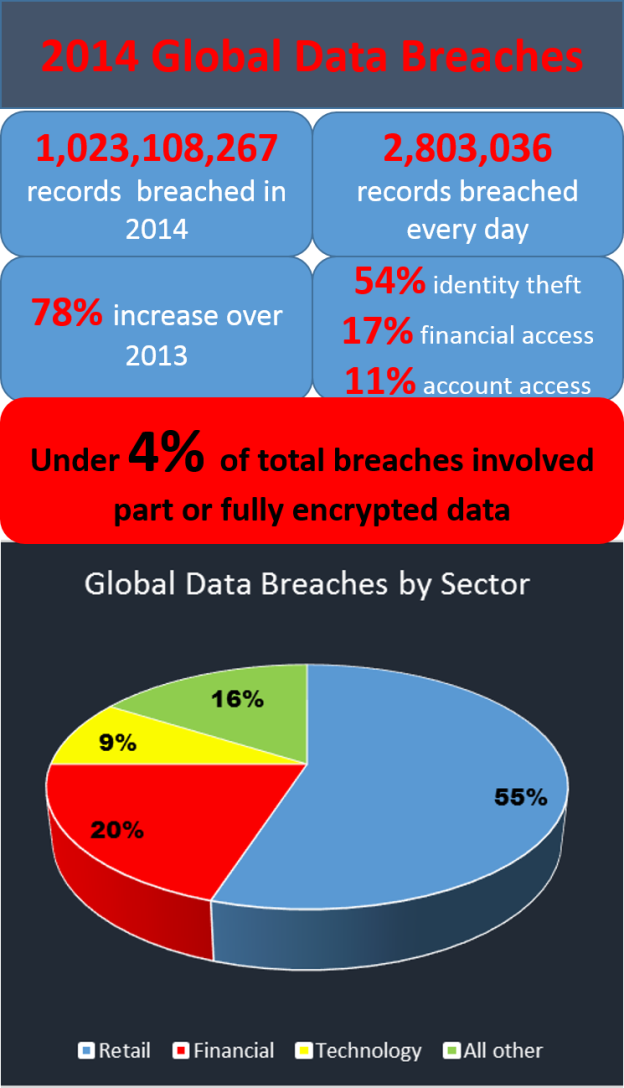 From the stats above, taken from the 2014 Year of Mega Breaches and Identity Theft, it’s clear to see:
From the stats above, taken from the 2014 Year of Mega Breaches and Identity Theft, it’s clear to see:
- the US is clearly the largest target, but UK has second largest number of breaches
- retail organisations suffered the greatest volume of data loss in 2014
- only 4% of data breaches involved encrypted data – an astonishing statistic which tells us:
- encrypted data is harder to breach
- given the critical nature of encryption in data protection, the sheer volume of unencrypted data is staggering – too many organisations are simply not taking the most basic of steps to help keep their data secure
ISO 27001 is an international standard for data security management, providing a risk-based approach to data security that involves a data governance standard that is embedded throughout the business covering processes, technology, employees and training.
In the past, obtaining ISO 27001 certification has been a time-consuming, arduous and costly exercise. Now, however, the whole process of creating the gap analysis, providing robust policies and procedures, and obtaining certification can be made much simpler.
If you’d like to know more about getting ISO 27001 quickly, simply and cost-effectively, please get in touch on 01787 277742 or email victoria@datacompliant.co.uk – we’ll be happy to have a chat and answer your questions
EU versus Google – £12 million DPA fine
 The pressure on Google over European data privacy issues has been ongoing for several years as EU data protection watchdogs attempt to bring the organisation – and other huge US companies – into line with European data protection principles.
The pressure on Google over European data privacy issues has been ongoing for several years as EU data protection watchdogs attempt to bring the organisation – and other huge US companies – into line with European data protection principles.
The latest threat to Google comes from Holland, where the Dutch DPA has threatened Google with a fine of up to 15M euros for breaking local laws over how it can use user data. Google has been given until the end of February 2015 to change the way it handles personal data, before the fine is levied.
Online behaviour used to target advertising
So what has Google done wrong? The issue is over the way Google uses data about people’s online behaviour to tailor advertisements. Google builds up a profile for every one of its users based on keywords used in searches, email messages, cookies, location data – even video viewing habits. However, it does not inform its data subjects that it is collecting and using data in this way, and nor does it obtain consent.
Google’s Data Assets
Google’s data is a core asset for the business, and other businesses like it. One of Google’s key data privacy issues is that the company has merged all its separate privacy policies into one policy which allows Google to share its user data across all its services – for example, Gmail data and search engine data can be used and combined across the company. In addition, there is no opt-out for the data subject.
From Google’s point of view, its customer profiling is enhanced considerably by this activity – and advertising to targeted customers is Google’s core revenue stream. Google also uses customer data to drive new products such as Google now (appointment based app, giving details on how to get to your appointment, where it is, what are the traffic conditions and what time to leave) – a great concept, but one that would be useless without Google’s ability to collect and use data from its users.
It has been clear for some time that the EU is determined to take on the challenge of the giant UK search engines and social media platforms, and curb the way they use data. Because Google has such a vast share of the market, it, in particular, regularly comes under fire from the EU.
Google Privacy Policy – Fairness and Transparency
The requirement for additional permissions or opt-outs may be more problematic than helpful for Google customers. But fairness and transparency is an issue that Google could address relatively simply – as a minimum the customer should be informed about the data Google is collecting about him or her, why it is being collected and how it is being used. And a little bit of creativity in the wording would serve to illustrate the benefits to the customer.
The single privacy policy makes such transparency difficult. So perhaps the simplest solution is to re-establish separate privacy policies for each of its business areas. That might at least serve to reassure not only the EU, but also the US data protection authorities who have also expressed concerns over Google’s single privacy policy.
Your thoughts and views are always welcome – please add your comments below. If you have any concerns about your data compliance in general or the impact of EU changes in your business, contact us on 01787 277742. Or email victoria@datacompliant.co.uk
EU Data Protection Regulation – Getting closer?
 The EU Regulation is designed to replace the current multiplicity of EU data protection laws with a single set of rules to be applied throughout all Member States. Time is moving on so it’s important to keep on top of the discussions and updates being published.
The EU Regulation is designed to replace the current multiplicity of EU data protection laws with a single set of rules to be applied throughout all Member States. Time is moving on so it’s important to keep on top of the discussions and updates being published.
Last month’s proposed revisions to Chapter IV (which deals with data controller and data processor obligations) are summarised below. However, it is worth remembering that “nothing is agreed until everything is agreed” in relation to the Regulation.
Greater discretion for data controllers – risk-based compliance
Businesses will be relieved to see greater discretion for data controllers in complying with the legislation as recent Chapter IV discussions in Europe have moved towards a risk-based approach to compliance.
A balance between privacy and entrepreneurship
 The proposed amendments to Chapter IV suggest that data compliance obligations should be proportional to the organisation’s specific data processing activity and associated risks.
The proposed amendments to Chapter IV suggest that data compliance obligations should be proportional to the organisation’s specific data processing activity and associated risks.
Once these activities and risks have been assessed, appropriate privacy and data protection tools should be instigated by the organisation.
Different activities, even where the same data is involved, may quite often have different consequences, requiring different levels of protection. The risk-based approach allows data controllers a more flexible approach in assessing their data compliance responsibilities within the context of their own particular business.
It appears that most countries welcome the risk-based approach, which they view as providing a good balance between protecting personal data and safeguarding businesses and entrepreneurship.
Chapter IV Proposed Revisions
Below are some examples of the revisions proposed by the EU Council:
- Data protection impact assessments are only required where “high” risk (for example identity theft, fraud or financial loss) to the rights and freedoms of individuals is involved
- The appointment of Data Protection Officers is voluntary (unless individual Member State legislation states otherwise)
- Only data breaches that are likely to result in “high risk for rights and freedoms of individuals” need be reported
- If stolen or breached data is encrypted or protected in such a way that the data remains indecipherable, there is no requirement to report the breach.
- Required levels of security measures will be established by considering multiple factors, including the nature, scope, context and purpose of the data processing to be undertaken, in combination with the cost of implementation and the technology available.
- Only where a data privacy impact assessment indicates that data processing would result in “high risk” to the rights and freedoms of individuals, the supervisory data protection authority should be consulted prior to the start of such processing
There is also a suggestion that data controllers may use “adherence of the processor to an approved code of conduct or an approved certification mechanism” to demonstrate compliance with the obligations of a controller. So organisations may find it well worth considering selecting only those data processors who have appropriate data security certification such as ISO 27001 or DMA DataSeal.
If you have any concerns about your data compliance in general or the impact of EU changes in your business, contact us on 01787 277742. Or email victoria@datacompliant.co.uk

CCTV Data Protection Guidelines from ICO
 Clearly surveillance has both benefits and drawbacks, and the level of public interest and debate about both is increasing. Technology is advancing swiftly, and surveillance cameras are no longer simply passively recording and retaining images. They are now also used proactively to identify people of interest, to keep detailed records of people’s activities both for social (eg schooling, benefits eligibility) and political (eg terrorist) reasons.
Clearly surveillance has both benefits and drawbacks, and the level of public interest and debate about both is increasing. Technology is advancing swiftly, and surveillance cameras are no longer simply passively recording and retaining images. They are now also used proactively to identify people of interest, to keep detailed records of people’s activities both for social (eg schooling, benefits eligibility) and political (eg terrorist) reasons.
There’s a real risk that, despite the benefits, use of CCTV can be very intrusive.
The ICO’s new CCTV code of practice continues its focus on the principles that underpinned the previous code of practice. However, it has been updated to take into account both the changes in the regulatory environment and the opportunities to collect personal data through new technology.
There is some fascinating information in the guidelines – specifically around some of that new technology, where three of the key recommendations are:
- Privacy Impact Assessments – a requirement that involves ensuring that the use of surveillance systems is proportionate and addresses a pressing need (see the
- Privacy Notices / Fair processing – a key issue for many of the new technologies is finding creative says of informing individuals that their personal data is being processed – particularly where such processing is simply not obvious.
- Privacy by design – for example, the ability to turn the recording device (audio and / or sound) on and off as appropriate to fulfil the purpose; the quality must be high enough to fulfil the purpose; the use of devices with vision restricted purely to achieve the purpose
The new technology specifically covered in the guide includes:
Automatic Number Plate Recognition (when to use it, data storage, security issues, sharing the data and informing individuals that their personal data is being processed – something of a challenge needing some creative thinking);
Body Worn Video (warnings against continuous recording without justification; the use of BWV in private dwellings, schools, care homes and the like – and, again, the thorny issue of informing subjects that they are being recorded);
Unmanned Aerial Systems drones are now increasingly used by businesses as well as the military (Amazon has stated its intention to use drones to deliver parcels …). Some of the key issues are privacy intrusions where individuals are unnecessarily recorded when the drone has some other purpose; the distinction between domestic and commercial use; providing justification for their use; the ability to switch the recording system on and off; the whole system of data collection, storage, accessibility, retention periods and disposal requires compliance.
Automated recognition technologies are increasingly used commercially to identify individuals’ faces, the way they walk, how they look at advertising and suchlike. Again, the issues of fair processing, degree of accuracy of images and their identification, storage, retention, transfer, disposal and security are all key to compliance.
If you are using surveillance devices to view or record and / or hold information about individuals, then it’s worth noting that such use is subject not only to the Protection of Freedoms Act (and its Surveillance Camera Code of Practice), and the Data Protection Act, but you also need to consider your obligations under The Freedom of Information Act 2000 and the Human Rights Act 1998.
If you have any concerns about your data compliance in general or your surveillance camera compliance specifically, contact us on 01787 277742. Or email victoria@datacompliant.co.uk

Surveillance Camera Code of Practice – 12 Principles
 Do you use a surveillance camera system within your organisation? If so, it’s worth noting that the Surveillance Camera Code of Practice must not only comply with the Data Protection Act and its 8 Principles, but also provides its own 12 guiding principles:
Do you use a surveillance camera system within your organisation? If so, it’s worth noting that the Surveillance Camera Code of Practice must not only comply with the Data Protection Act and its 8 Principles, but also provides its own 12 guiding principles:
- Purpose: Use of a surveillance camera system must always be for a specified purpose in pursuit of a legitimate aim, and necessary to meet an identified pressing need
- Privacy Impact: Use of a surveillance camera system must take into account its effect on individuals and their privacy, with regular reviews to ensure its use remains justified
- Transparency: There must be as much transparency in the use of a surveillance camera system as possible, including a published contact point for access to information and complaints.
- Accountability: There must be clear responsibility and accountability for all surveillance camera system activities including images and information collected, held and used.
- Policies and procedures: Clear rules, policies and procedures must be in place before a surveillance camera system is used, and these must be communicated to all who need to comply with them
- Relevance and Retention: No more images and information should be stored than that which is strictly required for the stated purpose of a surveillance camera system, and such images and information should be deleted once their purposes have been discharged
- Access to retained images and information should be restricted. There must be clearly defined rules on who may gain access for what purpose; the disclosure of images and information should only take place where it is necessary for such a purpose or for law enforcement purposes
- Standards: Surveillance camera system operators should consider any approved operational, technical and competency standards relevant to a system and its purpose, and work to meet and maintain those standards
- Security: Surveillance camera system images and information should be subject to appropriate security measures to safeguard against unauthorised access and use.
- Audit: Effective review and audit mechanisms should be in place to ensure legal requirements, policies and standards are complied with in practice. Regular reports to be published.
- Public Safety: When the use of a surveillance camera system is in pursuit of a legitimate aim, and there is a pressing need for its use, it should then be used in the most effective way to support public safety and law enforcement with the aim of processing images and information of evidential value.
- Accuracy: Any information used to support a surveillance camera system which compares against a reference database for matching purposes should be accurate and kept up to date.
If you have any concerns about your data compliance in general or your surveillance camera compliance specifically, contact us on 01787 277742. Or email victoria@datacompliant.co.uk

Smartphone Security
 Smartphones are becoming cleverer by the day. I use mine as an address book … to read books … listen to music … search the internet … look at emails … find my husband … use social media … keep track of the news … take pictures … and so much more. I even use it to make and receive calls and texts.
Smartphones are becoming cleverer by the day. I use mine as an address book … to read books … listen to music … search the internet … look at emails … find my husband … use social media … keep track of the news … take pictures … and so much more. I even use it to make and receive calls and texts.
But from a security point of view, smartphones can be leaky, and increasingly it’s down to the user rather than the provider to take responsibility for their own protection. Here is some simple guidance and some references for those who’d like more information:
Smartphones – as important as your wallet and credit / debit cards
Ofcom advises that you treat your smartphone as carefully as your wallet or a bank card, and that’s excellent advice. Losing your smartphone is inconvenient at best and a disaster at worst. There’s the potential expense of any charges that a thief might run up before you report it as lost. And, unless it’s insured, the cost of replacing a smartphone can be horribly expensive.
Not only that, but any confidential information is at risk – your contacts, your emails, even your bank account. And it’s no longer just your own data at risk. If you use your smartphone for business, losing it may have potentially serious implications for you and your company in the event of a data breach.
What to do before you lose your smartphone
- Set and use a pin or password both on your phone and your SIM for secure access
- Make sure you know your IMEI number – if you haven’t already done so, just type *#06# into your handset and it should flash up. If not, look behind your phone battery and you’ll find it there. Make a note of it and keep it somewhere safe.
- Have a look at Immobilisewhere you can register your phone and may then stand some chance of being reunited with it in the event of loss or theft. All UK police forces and various other lost property offices and agencies use it as an online database to trace owners of lost and stolen property.
- If you are registered with Immobilise, mark your phone as being registered – it just may help deter opportunistic theft
- Download an app such as findmyiphone or findmyphone. Not only will this help you trace your phone if it is lost or stolen, but it will also allow you to wipe details from it remotely to allow you at least to minimise theft of your data.
How to keep your data safe
- In the same way that you’d keep your computer data backed up, you should do the same for your smartphone – keep it backed up, either in the cloud or on some other device. That way you stand to lose the minimum amount of data.
- Keep up-to-date with your operating system – accept updates as they become available as they will include any fixes to security vulnerabilities within the previous software.
- Use antivirus software to protect your phone from attack by virus or spyware. I use Lookout, but there are various other excellent options.
- Make sure your apps are only downloaded from trusted sources. Check them out before you download them – read the reviews and check their privacy policies.
- Keep you apps updated when updates are offered.
- Bear in mind that a rogue app may allow access and control rights to a hacker who can then make calls, download content, send or intercept messages using your phone without your knowledge. You also run the risk that your smartphone becomes the entry point to other devices to which it may be connected.
- Check the permissions you grant when you download an app – for example, it may request to use your current location, or to access your photos etc. Make sure that you only provide the data that you require the apps to have, and ideally only provide the information the app needs in order to work.
What to do if you lose your smartphone
- If you lose your phone, contact your provider and (if you are insured) your insurer immediately.
- Get your phone blocked – to do this you’ll need to give your provider your phone’s IMEI number, make and model number.
What to do when you get rid of your phone
Before disposing of your smartphone, make sure that you:
- Erase any apps
- Erase any data held on it, including media cards
- Then go into your Settings menu and reset to Factory settings
Above all, smartphones should be treated as the valuable assets they really are, and kept safe to protect both personal and company assets data and assets.
If you have any concerns about your data security in general or your smartphone security specifically, contact us on 01787 277742. Or email victoria@datacompliant.co.uk

Data Protection and the ICO
Data Protection Complaints 2013 – 2014
Yesterday I read that the Information Commissioner’s Office handled 259,903 calls to its helpline and has resolved 15,492 data protection complaints last year. This is an increase of 10% over the previous year. And here’s another staggering figure – the ICO received 161,720 reports from people about spam texts and nuisance calls.
Half the total complaints received related to “subject access”, with a range of organisations about whom complaints were made, including lenders, local government, educational providers and local health providers.
The importance of data protection in business
Organisations and businesses can no longer ignore the importance of data protection governance, compliance and security – they now have no choice but to understand and meet their regulatory requirements to avoid the penalties of non-compliance. Last year’s attitude to and handling of ‘subject access requests’ is a perfect illustration of the current complacency seen among some data users.
The sheer volume of personal data being collected physically and digitally every day is multiplying at an extraordinary rate and organisations are continuing to find ever more complicated ways of using data. Use of big data continues to develop with organisations trying to navigate their way through woefully outdated legislation.
The importance of the ICO
As a result, the data protection challenges to business, the consumer and the ICO are spiralling. It’s increasingly important for the data subject to know that a strong, independent body – which means the ICO – can be trusted to keep watch and offer protection.
With this increase in volume and demand, it’s hardly surprising that the ICO is calling for greater powers, greater independence, and additional funding.
Funding is a particularly difficult area as the EU data protection reforms currently propose the removal of the notification requirement and accompanying fees that fund the ICO’s DPA work. Lack of funding will inevitably give rise to cuts in the services provided by the ICO – for example, it has no legal obligation to provide a helpline, and reduced funding makes it unlikely to be able to continue to handle its current – let alone future – volumes of calls a year.
So it’s absolutely vital not only to individuals but also to businesses, organisations, government and the ICO itself that necessary resource, funding, independence and evolving powers are provided to allow the Information Commissioner to continue to protect, update and enforce data protection legislation.
ICO’s internal data security breach
However, it is somewhat unfortunate that at the time the ICO is asking for greater funding, independence and stronger powers, they are also admitting to their own “non-trivial” data breach. The incident was treated as a self-reported breach and was apparently investigated and treated no differently from similar incidents reported to the ICO by others. After an internal investigation the ICO concluded that the likelihood of damage or distress to any affected data subjects was low, and that it did not amount to a serious breach of the Data Protection Act. A full investigation was carried out with recommendations made and adopted.
However, later information suggests that this breach is now linked to a criminal investigation. So the breach investigation has not, seemingly, been closed.
Data Compliant
If you have any concerns over data protection compliance or security, don’t hesitate to get in touch – call 01787 277742 or email victoria@datacompliant.co.uk
More delays to the European Data Protection Regulation?
 It is becoming increasingly difficult to say when the European Data Protection Regulation will come into force. The legislation is currently at the point where three-way negotiations need to take place between the Justice and Home Affairs Ministers, the European Commission and the European Parliament to finalise the text . It was broadly anticipated that the draft EU Data Protection Regulation would be passed later this year, making it law in the UK by 2016.
It is becoming increasingly difficult to say when the European Data Protection Regulation will come into force. The legislation is currently at the point where three-way negotiations need to take place between the Justice and Home Affairs Ministers, the European Commission and the European Parliament to finalise the text . It was broadly anticipated that the draft EU Data Protection Regulation would be passed later this year, making it law in the UK by 2016.
However, the recent European elections and new parties now represented in the European Parliament may impact the timescale of the passing of the Regulation and delay it even until early 2015, in which case it would become UK law in 2017. The new Parliament now needs to elect the MEPs to take part in the three-way negotiations, and reappoint members to its various committees etc to reflect the changes in party strength.
One of the interesting issues is that Viviane Reding has just been elected as MEP. In her role as Justice Commissioner, she has been an extraordinary force for the development and implementation of the DP Regulation. But as an MEP she will need to step down from her current role, and there is no guarantee that the new Justice Commissioner will be as driven in terms of getting the legislation passed.
So it is somewhere between difficult and impossible to determine when the European Data Protection Regulation will come into force in the UK, but it is increasingly unlikely to be before early 2017.
What has been clear since March, however, is that the legislation is coming, and businesses will benefit from being ready for the changes that it will bring. If you’d like any help assessing your readiness for the upcoming legislation, please contact Data Compliant on 01787 277742




