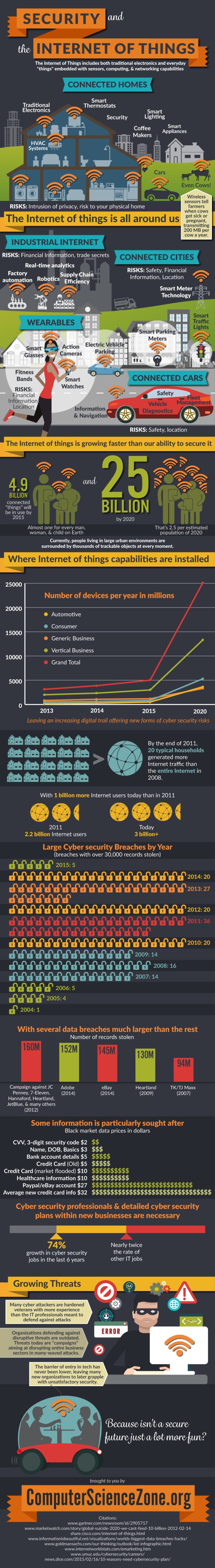
I was invited by ComputerScienceZone to share this fascinating infographic on my site – so here it is – a fascinating insight into the diversity and number of “things”, combined with the risks associated with the rapid growth and poor security.
Category Archives: Data Security
Data Security – A Summary
 When we talk about data security what do we actually mean?
When we talk about data security what do we actually mean?
Data security means protecting data, such as database, from destructive forces and from the unwanted actions of unauthorised users.
In the UK, the Data Protection Act is used to ensure that personal data is accessible to those whom it concerns, and provides redress to individuals if there are inaccuracies. This is particularly important to ensure individuals are treated fairly, for example for credit checking purposes. The Data Protection Act states that only individuals and companies with legitimate and lawful reasons can process personal information and cannot be shared.
The international standard ISO 27001 covers data and information security. Information security is the practice of defending information from unauthorised access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction. It is a general term that can be used regardless of the form the data may take (e.g. electronic, physical)
So what is Data Security?
- Data is any type of stored digital information.
- Security is about the protection of assets.
- Prevention is the measures taken to protect your assets from being damaged.
- Detection is the measures taken to allow you to detect when an asset has been damaged, how it was damaged and who damaged it.
- Reaction is the measures that allow you to recover your assets.
- Confidentiality ensures that that data is only read by the intended recipients.
- Integrity ensures that all of the data has not been corrupted from its original source.
- Availability guarantees that the data is usable upon demand.
- Accountability is audit information that is kept and protected so that security actions can be traced to the responsible party.
Audit Standards
Data Security is subject to several types of audit standards and verification, the most common are ISO 27001, PCI, ITIL. Security Administrators are responsible for creating and enforcing a policy that conforms to the standards that apply to their business.
IT certification audits are generally carried out by 3rd parties although regular internal audits are recommended. Clients can also carry out audits before they begin doing business with a company to ensure that their clients data is secured to their standards.
Security Policy
A security policy is a comprehensive document that defines a company’s methods for prevention, detection, reaction, classification, accountability of data security practices and enforcement methods. It generally follows industry best practices as defined by ISO 27001, PCI, ITIL or a mix of them. The security policy is the key document in effective security practices. Once it has been defined it must be implemented and modified and include any exceptions that may need to be in place for business continuity. Most importantly all users need to be trained on these best practices with continuing education at regular intervals.
Securing data
Data needs to be classified in the security policy according to its sensitivity. Once this has taken place, the most sensitive data has extra measures in place to safeguard and ensure its integrity and availability.
All access to this sensitive data must be logged. Secure data is usually isolated from other stored data and it is important that controlling physical access to the data centre or area where the data is stored is implemented.
Active Directory for example is used by many companies and is a centralised authentication management system that is used to control and log access to any data on the system.
Encryption of the sensitive data is critical before transmission across public networks. The use of firewalls on all publicly facing WAN connections needs to be in place and also the deployment of VLANs’ to isolate sensitive departments from the rest of the network. It is important to shut down unused switch ports. If Wi-Fi is deployed then it is important to use authentication servers to verify and log the identity of those logging on. Finally the deployment of anti-virus and malicious software protection on all systems.
Monitoring
Sometimes you will be surprised what you can find by simply walking around and look for passwords in the open, unattended screens.
Ensure that Event Viewer and Log Files are maintained this provides the audit trail. An Intrusion Detection/ Protection systems (IDS/IPS) to monitor the network and system activities for malicious activities or policy violations. Set up SNMP monitoring servers to monitor and alert for everything as this will alert Administrators to everything from unusual bandwidth usage to hardware failure. It is key to know what’s going on with your systems and network.
Documentation is also important, detailed network maps should be available as these maps make it easier to spot security weak points and any flaws in the design that could impact the data security.
You should also consider a network scanner that probes devices to ensure that they are secure. A network scanner will probe and report old out of date software, open ports and the give details on any potential exposures. Networks scans should be scheduled on a regular basis.
Keep up to date and stay Informed
Review log files regularly of any publicly facing server to see what types of attacks are being run against your enterprise.
Trade publications discuss the latest threats and technologies keeps you updated on the latest attack trends. It is important to understand the technology stack that you are protecting and the technology that is used to attack it.
User Education
Something which tends to not be given the required level of importance is user education. All relevant security policies must be clearly explained to the end users. A clear explanation of the consequences for violating these polices must also be explained. The end user needs to sign a document acknowledging that they understand the policies and consequences for violating these policies.
Enforcement
Any enforcement must obtain executive authority to enforce the business policies and procedures. This must be based on a systematic approach of warnings and punishments.
The author, Tony Schiffman, is Data Security Director at Data Compliant. If you have any concerns about your organisation’s data security or vulnerabilities and you’d like a chat, please call Tony on 01787 277742 or email dc@datacompliant.co.uk
Data Security – Phishing
45% of phishing attacks are successful, according to Google’s December 2014 report. Indeed, the infamous 2013 Target data breach was due to a successful spear phishing attack on one of the company’s suppliers. The reported cost to the business was a massive $162M plus additional expenses resulting from class action lawsuits and reputational damage.
Many data breaches are a direct result of the attacker using individuals or employees to access systems or data, and it’s worth noting that 58% of large organisations and a third of SMEs fall prey to staff-related data breaches (*UK 2014 Information Security Breaches Survey).
With that in mind, I thought it would be helpful to summarise some points to help recognise and deal with phishing emails.
What is phishing?
Phishing is a deceptive means of trying to acquire personal information such as your identity or data that you hold and access – for example your user name, passwords, credit card details, contact directories and so on. Phishing is typically carried out by email or instant message, which may ask you to provide the data directly, or it may send you to a website or phone number where you will be asked to provide data.
Why Phishing Works
A phishing effort can be hard to recognise, particularly if it comes from a source that you are inclined to trust – for example a friend or colleague (who may have been phished themselves), or your bank, social media site, telephone provider etc.
- Phishing emails are designed to look like real emails from real, sometimes large, reputable organisations.
- They are likely to seem to come from an organisation or individual you know and would expect to hear from – for example your bank or building society, your insurer, a business with whom you are in regular contact, your social networking sites, an online auction site or even a friend whose email sits in your address book
- They may look absolutely authentic, including using legitimate logos
- They may well contain information that you would not expect a scammer to know – for example personal data (that they may, for example, have picked up from one of your social networking sites)
- They may include links to websites which will require you to enter personal information – and that website may also look very similar to the legitimate website it is pretending to be.
How to spot a phishing email
There are ways to recognise and avoid being caught out by fraudulent emails or the links they contain.
- Are you expecting the email you’ve just received? Any email which asks you for personal information or log in details or to verify your account must be treated with caution – most reputable companies will never ask for your personal details in an email
- Don’t be pressured just because the email looks urgent
- Beware of attachments – these may pretend to be an order summary or an invoice for immediate payment or a receipt or any manner of other things. If you haven’t placed an order, or your bill is already paid, then be careful. If in doubt, simply do not open the attachment.
- Check the email’s spelling, grammar and formatting – if they’re not correct, treat the email as suspicious
- Never respond to an email that asks you to update your credit card or payment details
- Watch out for free giveaways with links to websites – it’s likely that such websites will attempt to embed a virus into your computer which allows them to capture your keystrokes to get your login details or financial details such as your bank account
How to spot a phishing link?
Such links are likely to include all or part of the legitimate website address.
- Be aware than any change to the legitimate address may lead to a false website – a spelling mistake, a missing letter – just one character’s difference can take you somewhere you just don’t want to go,
- It is generally safer to go to the online website using your own bookmarks or by typing in the website address yourself
- Where a website link is provided, it may be “masked” so that what you see will not take you where you expect. Using your mouse to “hover” your cursor over the link may enable you to see the actual address – DO NOT CLICK ON ANY LINK unless or until you are completely certain it is the legitimate website
Protect against phishing
Being aware and understanding how to spot a potential phishing effort is helpful, but additional steps should be taken to protect your computer and system against such attacks. There is no single solution – the best option is to adopt a multi-layered approach:
- Good security software will help to prevent successful phishing by spotting “bad” links and blocking fake websites.
- While not providing all-encompassing protection, anti-virus, anti-spyware and anti-malware applications should be used, and kept up-to-date. Ensure that at least two different supplier technologies are in operation.
- Ensure that all firewall settings should be used and updated regularly to help prevent phishing and block attacks.
- Subscribe to cyber-intelligence services which may be used to identify on-line threats, misrepresentations, or online fraud’s targeting brands – for example, RSA or Verisign
- Ensure that applications and operating systems are up-to-date and fully patched
What to do if you have opened a phishing email
Just opening the email is unlikely to cause a problem. However, it is helpful to report phishing emails:
- To the ISP (internet service provider) that was used to send you the email so that ISP provider can close the sender’s email account
- If “report spam” buttons are available, use them
- Report the email to the legitimate organisation the sender is pretending to be
- Delete the email from your device
- Inform your IT department and / or your data protection / data compliance / data security officer
- Report the phishing email to Action Fraud – the UK’s national fraud and internet crime reporting centre – at https://reportlite.actionfraud.police.uk/
What to do if you click on a phishing link
- Immediately run a virus check on your computer whether or not you have provided any personal details
- Change your password for organisation which the phisher is mimicking
- If you use the same password for multiple accounts, you need to change all these passwords too
- Notify the relevant financial organisation(s) if you have entered banking or credit card information
- Inform your IT department and / or your data protection / data compliance / data security officer
- Report the phishing email to Action Fraud at https://reportlite.actionfraud.police.uk/
As phishing attacks predominantly targeting end-users, it is a good idea to invest in a security education and awareness programme to raise the profile of risk. It’s also helpful to include your clients in such a programme.
If you have any concerns about your organisation’s vulnerability to phishing attacks and you’d like a chat about staff training or prevention, just call 01787 277742 or email dc@datacompliant.co.uk
Data Compliant Services
ISO 27001 Certification – who needs it?
It’s becoming an increasingly essential part of due diligence that a data controller, when appointing a data processor, will ask one simple question: “Do you have ISO 27001 Certification?” Given that data controllers are the liable parties for any data breaches or lack of compliance, they need to be certain their data is to be processed safely. So if the answer is “no”, the processor is unlikely to win the contract unless they have some other extraordinary and unique competitive advantage.
I was going to write a blog about why ISO 27001 certification is so important. Then I thought it would be simpler just to show you. It’s all about protecting your business from potential breaches.
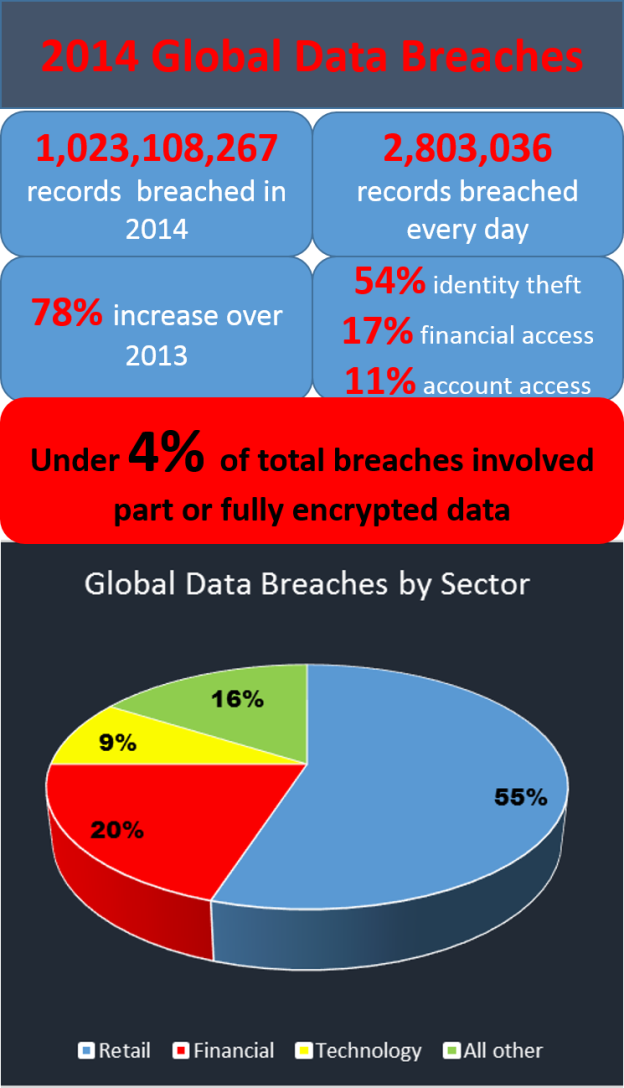 From the stats above, taken from the 2014 Year of Mega Breaches and Identity Theft, it’s clear to see:
From the stats above, taken from the 2014 Year of Mega Breaches and Identity Theft, it’s clear to see:
- the US is clearly the largest target, but UK has second largest number of breaches
- retail organisations suffered the greatest volume of data loss in 2014
- only 4% of data breaches involved encrypted data – an astonishing statistic which tells us:
- encrypted data is harder to breach
- given the critical nature of encryption in data protection, the sheer volume of unencrypted data is staggering – too many organisations are simply not taking the most basic of steps to help keep their data secure
ISO 27001 is an international standard for data security management, providing a risk-based approach to data security that involves a data governance standard that is embedded throughout the business covering processes, technology, employees and training.
In the past, obtaining ISO 27001 certification has been a time-consuming, arduous and costly exercise. Now, however, the whole process of creating the gap analysis, providing robust policies and procedures, and obtaining certification can be made much simpler.
If you’d like to know more about getting ISO 27001 quickly, simply and cost-effectively, please get in touch on 01787 277742 or email victoria@datacompliant.co.uk – we’ll be happy to have a chat and answer your questions
Phishing, e-commerce and retail
Britain is targeted by up to 10,000 cyber attacks per hour, making it a business imperative for organisations to strengthen their data security systems and processes.
Retail and financial services websites are at the highest risk from attack, and Christmas – with a projected online spend of £17.4bn** – is the most popular time of year for cyber criminals.
A Google study from a couple of weeks ago made an astonishing statement:
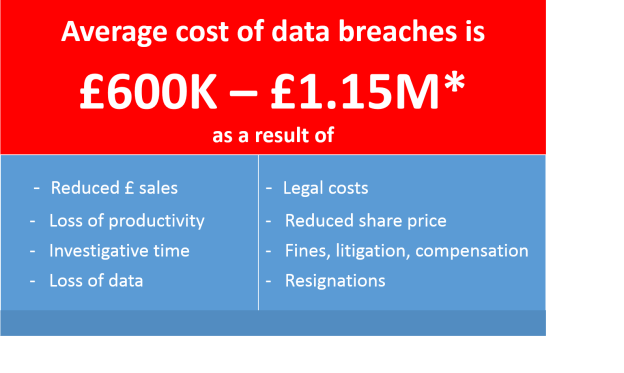
This is a particularly worrying statistic given that data security breaches carry a huge cost – both to reputation and financially.
The costs of a breach increase every year, and will inevitably continue to rise as new legislation comes in with greater powers to the ICO.
So it’s time for retailers to make sure their staff don’t fall into the 45% of successful phishing attacks, and understand how to minimise security risks to the business.
25% Christmas Discount
Data Compliant provides data security training workshops for companies who want their employees to understand how to keep their data secure.
2-hour security workshops for up to 10 attendees per session are available from January 5th 2015. The usual cost is £1,100*. Within the workshop, we’ll demonstrate how to recognise and avoid phishing attacks.
Any organisation making a firm booking for a data security workshop before 23rd December will receive their 25% discount – ie a reduction in cost from £1,100 to just £825.*
For more information or to book your workshop, call 01787 277742 or email victoria@datacompliant.co.uk
* Stats taken from UK 2014 Information Security Breaches Survey – Department for Business Innovation and Skills
**stats from internetretailing.net
* Costs exclude VAT and expenses.
Smartphone Security
 Smartphones are becoming cleverer by the day. I use mine as an address book … to read books … listen to music … search the internet … look at emails … find my husband … use social media … keep track of the news … take pictures … and so much more. I even use it to make and receive calls and texts.
Smartphones are becoming cleverer by the day. I use mine as an address book … to read books … listen to music … search the internet … look at emails … find my husband … use social media … keep track of the news … take pictures … and so much more. I even use it to make and receive calls and texts.
But from a security point of view, smartphones can be leaky, and increasingly it’s down to the user rather than the provider to take responsibility for their own protection. Here is some simple guidance and some references for those who’d like more information:
Smartphones – as important as your wallet and credit / debit cards
Ofcom advises that you treat your smartphone as carefully as your wallet or a bank card, and that’s excellent advice. Losing your smartphone is inconvenient at best and a disaster at worst. There’s the potential expense of any charges that a thief might run up before you report it as lost. And, unless it’s insured, the cost of replacing a smartphone can be horribly expensive.
Not only that, but any confidential information is at risk – your contacts, your emails, even your bank account. And it’s no longer just your own data at risk. If you use your smartphone for business, losing it may have potentially serious implications for you and your company in the event of a data breach.
What to do before you lose your smartphone
- Set and use a pin or password both on your phone and your SIM for secure access
- Make sure you know your IMEI number – if you haven’t already done so, just type *#06# into your handset and it should flash up. If not, look behind your phone battery and you’ll find it there. Make a note of it and keep it somewhere safe.
- Have a look at Immobilisewhere you can register your phone and may then stand some chance of being reunited with it in the event of loss or theft. All UK police forces and various other lost property offices and agencies use it as an online database to trace owners of lost and stolen property.
- If you are registered with Immobilise, mark your phone as being registered – it just may help deter opportunistic theft
- Download an app such as findmyiphone or findmyphone. Not only will this help you trace your phone if it is lost or stolen, but it will also allow you to wipe details from it remotely to allow you at least to minimise theft of your data.
How to keep your data safe
- In the same way that you’d keep your computer data backed up, you should do the same for your smartphone – keep it backed up, either in the cloud or on some other device. That way you stand to lose the minimum amount of data.
- Keep up-to-date with your operating system – accept updates as they become available as they will include any fixes to security vulnerabilities within the previous software.
- Use antivirus software to protect your phone from attack by virus or spyware. I use Lookout, but there are various other excellent options.
- Make sure your apps are only downloaded from trusted sources. Check them out before you download them – read the reviews and check their privacy policies.
- Keep you apps updated when updates are offered.
- Bear in mind that a rogue app may allow access and control rights to a hacker who can then make calls, download content, send or intercept messages using your phone without your knowledge. You also run the risk that your smartphone becomes the entry point to other devices to which it may be connected.
- Check the permissions you grant when you download an app – for example, it may request to use your current location, or to access your photos etc. Make sure that you only provide the data that you require the apps to have, and ideally only provide the information the app needs in order to work.
What to do if you lose your smartphone
- If you lose your phone, contact your provider and (if you are insured) your insurer immediately.
- Get your phone blocked – to do this you’ll need to give your provider your phone’s IMEI number, make and model number.
What to do when you get rid of your phone
Before disposing of your smartphone, make sure that you:
- Erase any apps
- Erase any data held on it, including media cards
- Then go into your Settings menu and reset to Factory settings
Above all, smartphones should be treated as the valuable assets they really are, and kept safe to protect both personal and company assets data and assets.
If you have any concerns about your data security in general or your smartphone security specifically, contact us on 01787 277742. Or email victoria@datacompliant.co.uk


Data Compliance and Cloud Computing
It’s clear that the innovative and accessible technical services provided by cloud computing are increasingly being selected and used by businesses. And there are good reasons for doing so – not least accessibility, cost, reliability, resilience, and innovative products. However, there are also risks to data protection which data controllers need to consider and be sure that such their cloud processing activity complies with the Data Protection Act.
What is cloud computing?
Cloud computing covers a broad range of services and technology, but the Information Commissioner’s Office (ICO) defines it as:
“access to computing resources, on demand, via a network”
To explain:
Resources include storage, processing, software
On Demand simply means that the resources are available to the customer or user on a scalable, elastic basis, typically through virtualised resources
Via a Network refers to the transit of data to and from the cloud provider, which may be over a local or private network, or across the internet.
The Data Protection Act (DPA) and Cloud Computing
All operations involving personal data that take place in the cloud – including storage – must comply with the DPA, and it is the data controller who has ultimate responsibility for that compliance.
However, if layered cloud services are being used (eg different cloud providers of software, platforms or infrastructure) then it’s quite possible that there will be a number of data controllers and data processors working together to deliver services which included processing personal data.
The cloud customer is most likely to be the data controller, and will therefore have overall responsibility for complying with the DPA. However, depending on precisely the role of the cloud provider, the customer must assess whether the cloud provider is simply a contracted data processor or is, indeed, a data controller in its own right – which may be the case if a cloud provider in any way determines the purpose(s) for which the personal data are to be processed. In this case the cloud provider will be responsible for its own data protection compliance.
12 Cloud-specific DPA Considerations
 There are some specific considerations for data controllers who have moved or are considering moving personal data to the cloud. Below are twelve:
There are some specific considerations for data controllers who have moved or are considering moving personal data to the cloud. Below are twelve:
- What personal data is to be processed (and how) in the cloud, and what are the inherent data protection risks
- What steps can be taken to mitigate those risks (eg authorisation protocols)
- Who is the data controller
- What additional personal data may be collected in the cloud (eg usage stats, transaction histories of users and other such ‘metadata’)
- Does the cloud customer’s privacy policy provide adequate information about processing data in the cloud
- Does the cloud customer need to run a privacy impact assessment to identify any privacy concerns and address them from the beginning of the process
- Does customisation of an existing cloud service cause any additional privacy risks
- What monitoring, review and assessment requirements between cloud customer and cloud provider should be put in place to ensure the cloud service runs as expected and to contract
- What commitment does the cloud provider have to keep the cloud customer informed in the event of changes in the chain of sub-processors taking place during the provision of the cloud service
- A written contract is required by the DPA between the data controller and the data processor – beware of a cloud provider which offers terms and conditions with no opportunity for negotiation. The risk that those terms and conditions may subsequently change needs to be taken into consideration.
- The data controller is responsible for the security of its data processor – assessment of the security of the cloud provider is mandatory
- Data outside the UK / EEA – the data controller must check the countries where data is likely to be processed and satisfy itself that the relevant security arrangements are in place
8 Essential Policies and Processes
 Any business will benefit from formal, documented policies and procedures. Having made a decision to use cloud services, there are some specific requirements that are particularly important from a personal data compliance perspective:
Any business will benefit from formal, documented policies and procedures. Having made a decision to use cloud services, there are some specific requirements that are particularly important from a personal data compliance perspective:
- Access control – the data is, by the nature of cloud computing, accessible from any location – home, the office or on a range of devices. Sufficient measures need to be put in place to prevent unauthorised access to the data
- Authentication processes – to verify that a cloud user is authorised to access the data
- A system is required to create, update, suspect and delete user accounts
- Leaver protocols need to be put in place
- Data retention and deletion policies are required – consider your cloud provider’s deletion issues across multiple locations and back-ups
- Cloud provider access policies need to be in place for occasions when the cloud provider needs access in order to provide services
- Staff training on cloud processes and controls is required to maintain the security of the cloud service
- Regular audits of procedures and policies in place will help ensure ongoing compliance
The cloud is here to stay. If you’d like any information or have any concerns about your own cloud provider contracts, policies or compliance issues, please don’t hesitate to contact us:
victoria@datacompliant.co.uk
01787 277742
Data Security – Microsoft Office XP and 2003
 On 8 April 2014 , office support for Microsoft’s Windows XP and Microsoft Office 2003 will come to an end. Not the end of the world, you’d think, but if your organisation keeps personal information on those versions, this is a significant problem.
On 8 April 2014 , office support for Microsoft’s Windows XP and Microsoft Office 2003 will come to an end. Not the end of the world, you’d think, but if your organisation keeps personal information on those versions, this is a significant problem.
Though PCs will continue to run, the issue is that Microsoft will not be providing any further updates or fixes to these products. This means that in the event of any security flaw, your system will be vulnerable, and so in turn will any personal data you hold.
It is inevitable that, over time, attackers will increasingly find the vulnerabilities within these products, which will provide them with more and more opportunities to access and manipulate your systems. To prevent the risk of personal data breaches in these circumstances, the best advice is to migrate to a supported system before the deadline of 8th April.
It’s not just Microsoft where stopping system support is an issue – the same is true of other providers who do not support their systems. So it’s well worth making sure that you and your organisation have ‘appropriate technical organisational measures in place to keep individuals’ personal data safe.
Failure to do so puts you in breach of the Data Protection Act, and the ICO has the power to levy a fine of up to £500,000 to any organisation whose failure to comply with the DPA has led to serious issues of data security.
The size of fine varies enormously depending on the scale and potential damage caused by the breach. For example the ICO has recently fined the British Pregnancy Advice Service £200,000 after a hacker obtained thousands of individuals’ personal details due entirely to poor data security. And, on a smaller scale, the owner of a loans company, Jala Transport, was fined by the ICO after his car was broken into. The thief stole £3,600 and a hard drive. Even though the hard drive was password protected, the data within was not encrypted and it included customers’ names, dates of birth, payments made, and the identity documents provided to support the loan application. His fine could have been as high as £70,000, but was reduced to £5,000 to reflect the limited financial resources of the company and the fact that the breach was reported voluntarily.
In both cases, the breaches were perpetrated by a malicious third party. But it was the lack of the businesses’ security and protection of the personal data that was the root cause of the fines. This is why it is so important that companies remain ready for the security issues which will inevitably arise when their service providers switch off support – whether the provider is Microsoft or another.
Data Compliant helps businesses build policies and processes to enable them to become and remain secure and compliant both in terms of systems and governance – if you have any concerns over your data security, don’t hesitate to contact us on 01787 277742 or email tony@datacompliant.co.uk
Data Protection – Security Basics
This article has been written to help companies, particularly SMEs, understand the significance and importance of strong data security and excellent staff training, specifically in relation to data protection compliance within their own businesses when dealing with personal and sensitive data.
Apart from the obvious necessity to keep your premises physically secure, and shred any confidential paperwork, there are four main areas covered by this article:
- Computer Security
- Encryption
- Emails
- Staff Training
Computer security
Protecting your computers and computer networks includes a number of steps, which can be relatively simple and straightforward to implement. As is often the way, anything is simple if you know what to do and how to do it. For example, simple security steps include:
- Protection Installing firewalls and virus-checking tools
- Updates Keeping the operating system updated automatically ongoing
- Security updates Staying aware of the latest security patches and updates, and downloading when available
- Anti-spyware Consider installing anti-spyware tools (to prevent hostile individuals from monitoring your computer activity, and from making malicious attacks against you.
- Back-ups are an essential part of computer hygiene – regular backups should be taken and kept separately so that if your computers are lost, you still have the information available.
- Disposal When you get rid of a computer, it is vital to ensure that all personal information before you move it on. I always remove the hard drive, and smash it into small pieces – which is probably overkill, but it works for me! There are other “technical” solutions, but I prefer to destroy the hard drive and know that it’s gone for ever.
- Spam filters Ensure that you either have spam filters on your computers or that you use an email provider that offers this service.
Encryption
If sensitive personal information is stolen or lost, it is highly likely to cause damage or distress. To minimise the risk of disclosure, any such personal information really should be encrypted. The truth is that login usernames and passwords offer only minimal protection – absolutely not enough to protect against illegal – or simply unauthorised – access. It is also worth remembering that enormous volumes of data can now be stored on tiny devices from memory sticks to smartphones.
Encryption can be a tricky area, so if you are uncertain of how encryption works, or the strengths and weaknesses of various types of encryption, Tony Schiffman can provide useful advice on how to keep your information secure. Just drop him a line at tony@datacompliant.co.uk
email security
Writing, sending and receiving emails is now taken for granted as just a part of everyday life. This may be why there are so many varied opportunities for error and carelessness. Some of the most common issues are summarised below:
- if the contents of an email are sensitive, the email should be encrypted or password protected.
- when you start to type in the name of the recipient, your software may automatically suggest similar addresses which you have used before. For example, I have a few Johns in my address book whom I email regularly. Each time, the auto-complete function offers me several Johns and I have to force myself to remember to check that I have picked up the right address before clicking “send”.
- Group email addresses are a useful tool, but it is always worth double-checking who is included within the group and be certain that you eliminate anybody who should not receive your message.
- If you want to copy someone on an email, but don’t want to share their email address, use the bcc function rather than the cc. When you use cc, all recipients will be able to see he email addresses of all other recipients to whom the email was sent.
Interesting (if irrelevant) note –we still use the term cc, which stands for carbon copy – going back to the days of typewriters when a sheet of coated carbon paper was placed between two or more sheets of paper. The pressure of the typewriter keys on the carbon papers would cause the ink to be transferred to the additional sheet(s) of paper, thus providing carbon copies. Bcc, of course, stands for blind carbon copy.
- When sending a sensitive email from a secure server to a recipient whose server is insecure, the security of that email will be jeopardised. Always check the security of your recipient’s server / provider before sending your message.
- Use spam filters on your computers, or use an email provider that offers spam filtering services.
Staff Training
Training your staff to keep data secure is also vital. Staff can be held responsible for data compliance breaches and may sue their company if they have not been given essential training.
Did you know that your staff can be prosecuted if they deliberately give out personal details without permission? So it’s essential that their access to personal or sensitive data is limited purely to what they need to do their job, and they are trained to understand what they can and cannot do. For example:
- Discretion Your staff may receive enquiries from people who are trying to obtain personal details dishonestly – teach them how to handle such enquiries so that they cannot be tricked into providing inappropriate information.
- Passwords Ensure your staff use strong passwords. The longer the better, and greater strength can be gained by combining letters, numbers, punctuation and other special characters, while using both upper and lower case letters.
- Confidentiality It is, of course, essential that members of staff do not share their passwords or knowledge of sensitive or personal data with colleagues or friends.
- Professionalism Staff members should be trained to be professional in their communications, and avoid any offensive communications, emails, or inappropriate dissemination of the details of other people or their private lives. They must be trained to understand that their inappropriate behaviour can bring your business into disrepute.
- Spam They should not open spam – not even to unsubscribe or ‘request no further mailings’. If you do not have spam filters on your computers, when they receive spam, your staff members should be instructed that, when they receive spam, the email should be deleted.
- Financial information They should be taught not to believe emails that appear to come from a bank or building society that asks for account or credit card details or password information
If you would like to discuss staff training with Data Compliant, please contact victoria@datacompliant.co.uk
Data Breaches
Data security falls into a number of areas. Based on the ICO’s stated data breaches from April to July 2013, it is clear that security and staff training are critical elements in protecting the personal data you hold. The types of breach noted during that period are illustrated in the diagram below. It is notable just how significant security and staff training are in the prevention of protecting personal and sensitive data.
In our marketing and data consultancy, Tuffill Verner Associates, we have helped businesses navigate data permissions and compliance across B2C and B2B. With over 30 years experience each, Victoria Tuffill and Michelle Evans are well placed to help marketers stay compliant while still achieving their marketing goals. We provide clear, tailored practical and creative advice to marketers to solve the difficulties of achieving results while staying within the confines of legal compliance.
If you’d like to chat about your data compliance, security or governance needs, please contact Victoria or Michelle on 01787 277742 or by email – victoria@datacompliant.co.uk or michelle@datacompliant.co.uk